Windows has a great new feature which helps notify you when you may have inadvertently pirated your copy of the operating system. This feature is really handy, because sometimes people will slip and fall and accidentally steal a copy of Microsoft Windows.
Windows Genuine Advantage will detect this situation and provide you with valueable feedback so that you may address the issue by going out and buying a new copy of the operating system and reinstalling.
Here is a screenshot of WGA in action:
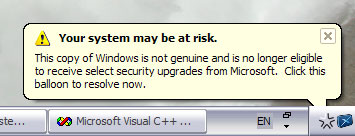
Now, I greatly appreciate this information. I for one would immediately take corrective action if my copy of Windows was actually pirated.
Fortunately, sometimes your situation is a little different. Maybe an innocent user has, one way or another, lost possession of their original product key. Tornado, earthquake, fire, air raid, black holes and ninja stars are some possible ways this could occur.
What do you do in this situation? Now, it seems rather silly to go buy another product key – just because you lost yours. It’s a simple misunderstanding.
Luckily, Microsoft was polite and left the binaries for WGA lightly protected. This means you can easily go in and inform WGA that you have, in fact, purchased your copy of Windows.
There are programs out there to make this modification for you. I took a slightly different approach, however, and decided that I would like to keep the warning message bubbles. I just wished to slightly modify the contents of those messages.

Now, whenever I come back to my computer – and sometimes just at random moments – WGA gives me a few words of appreciation. What used to be a depressing accusation of guilt, is now replaced with a friendly greeting! How nice.
The change is simple. Just pop open the WGA app in your favorite hex editor or resource editor, and search for the original messages. Replace with a message of your choice, and voila – your own personal motivational notification program.
c:WINDOWSsystem32WgaTray.exe


Next, just open up task manager and kill the process “WgaTray.exe”. Don’t worry, it is such a user-friendly program that it will automatically restart itself!












